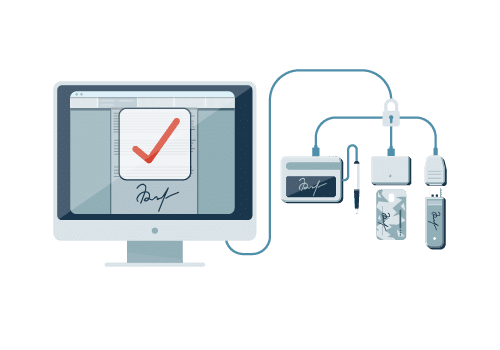
SigniFlow Security Features
Confidence in Posture
Book a Demo
Managed XDR: The Ultimate Cybersecurity Solution

SOC (System and organisation Controls) 2 Level Protection Managed WAF
Uptime Monitoring and Reporting

Application Security
We are dedicated to enhancing the security and trustworthiness of the SigniFlow application through continuous development, addition, and rigorous testing of security features.
- All communication between the customer and the SigniFlow Cloud is encrypted using industry-standard 2048-bit TSL encryption, which rules out man-in-the-middle attacks and eavesdropping.
- Certified ethical hackers regularly carry out penetration testing on the SigniFlow Cloud, to ensure port and penetration safety.
- Databases are encrypted using the latest SQL server encryption.
- SigniFlow server and user access are tightly managed, and two-factor authentication is applied for administrative access.
- Data backups are performed daily.
- The SigniFlow application has a modular design, catering to multiple deployment methods with multiple layers of security.

Protected Audits
SigniFlow is the only digital signature application that embeds and protects each signer’s audit events, using steganography and cryptography.
- This method ensures audit logs fully comply with the most stringent of measures for non-repudiation.
- Write-once-read-many (WORM) methodology is followed to write each time-stamped audit event as data bits, hidden in the graphic (electronic signature layer), using steganography. This is then cryptographically sealed by each digital signature event.
- The full audit log, linked to the unique document ID, can be retrieved by running the PDF through a steganography decoder.

Signature Security
Digital Certificates
SigniFlow digital signatures are created using digital X.509 certificates with built-in Private/Public Key Infrastructure (PKI) capabilities, which are verifiable by using free Adobe Acrobat© visual-trust indicators.Long-Term Validation
SigniFlow supports long-term digital signatures. These signatures have embedded timestamps and verification information, such as CRL and OCSP, to prove the time of signing and certificate validity.Tamper-Evident
When a user signs, we apply the latest security protocols, cryptographic algorithms and key lengths endorsed by governments and banks, to protect the content of the document and make every transaction tamper-evident.
PAdES Part 2
ISO 32000-1 original PDF Signature format. SigniFlow’s approval signatures have the embedded evidence information for Long-Term Validation (LTV) and trusted Timestamp Services.PAdES Part 3
Our signatures are based on the EU Qualified Signature format (CAdES-EPES), which is the latest PDF signature format. This allows for policy information to be added to the digital signature, for identification of the policy rules for applying and verifying such signatures.PAdES-Basic
Includes the electronic signature itself, ensuring the integrity of the signed document. Typically based on a digital certificate issued by a trusted Certificate Authority (CA). Provides basic validation and authentication of the signer's identity.PAdES-BES (Basic Electronic Signature)
Builds upon PAdES-Basic by adding more detailed information about the signing process. Includes signer identity information, signing time, and details of the digital certificate used. Offers enhanced validation and verification capabilities compared to PAdES-Basic.PAdES-EPES (Explicit Policy Electronic Signature)
Incorporates a predefined signature policy explicitly stating the technical and legal requirements for the signature. Guarantees compliance with specific regulations or standards by adhering to the defined policy. Provides additional assurance regarding the validity and legality of the electronic signature.PAdES-LTV (Long-Term Validation)
SigniFlow ensures the long-term validity and integrity of electronically signed documents. It includes all the necessary elements for validation, even as technologies change or certificates expire. We use timestamping and embedding certificate revocation information to maintain validity over time.We provide support at all levels of PAdES, ensuring regulatory compliance and legal validity across various industries and jurisdictions.
Furthermore, we seamlessly integrates with multiple Certificate Authorities (CAs), including those participating in the Adobe Approved Trust List (AATL) and the European Union Trust List (EUTL). This integration allows you to obtain digital certificates from trusted CAs and achieve regulatory-compliant signatures tailored to your needs, regardless of industry or geographical location.
By leveraging SigniFlow's capabilities, you can confidently adopt electronic signatures for your document workflows, knowing you meet the regulatory requirements and standards for electronic transactions.
Disaster Recovery
In the unlikely event of a disaster - whether natural or human-induced - our disaster recovery tools, policies and procedures will ensure the retrieval and continuation of our vital systems and infrastructure.
- Our servers are segregated over multiple regions.
- Depending on the disaster region, we will divert traffic to a separate specified environment, and the affected server(s) will recover to a different designated failover location using our end-to-end backup and disaster recovery process.
- Depending on the incident at hand, there may be a variety of external parties that will be communicated with during the response.
- We have service-level agreements in place with all external parties to ensure that we can recover services as quickly as possible.

24/7 Online support
We understand your office hours. SigniFlow offers 24/7 online support to all customers.
No matter where you are and no matter what time it is, we are always online to help you meet your deadlines.